Next Generation Firewall NGFW®
Global linkage | Coordinated defense | Asset awareness | Security visibility
Next Generation Firewall NGFW® Overview
Topsec next-generation firewall system integrates AI-driven unified intelligent detection engine and combines multiple security modules such as intrusion prevention, WAF, TVD, URL filtering, DDoS protection, HTTPS traffic detection, advanced threat protection, anomalous behavior analysis, DLP, threat intelligence, linking various network devices of the cloud, management and endpoint, ultimately providing users with an intelligent, proactive and secure “zero-dead-angle” comprehensive protection solution that integrates AI single-point defense, multiple intelligent synergies and cloud detection empowerment.
Product Advantages
AI-driven intelligent detection engine
The built-in AI-driven integrated intelligent detection engine can not only handle traditional security services such as anti-virus protection and intrusion detection and prevention, but also detect DGA domain names, covert channels, malicious encrypted traffic, and block their communication processes, thus effectively defending against a wide range of advanced threat attacks that were difficult to detect in the past.
Data leakage protection
Based on the two basic modules (keyword data filtering and file filtering), for encrypted traffic of commonly used web application protocols, files are restored through SSL decryption, and the content of restored files will be matched to block or release encrypted data flows. The system can effectively block malicious visitors from hacking the website databases and stealing service data or other sensitive information by means of SQL injection, web page Trojan horses, and other attacks.
Converged defense against malicious software
The system has an independent malicious software detection and defense engine, and has two rule libraries (malicious software feature library and botnet feature library). The system can not only detect and defend against malicious code such as new zombie viruses, Trojan horses, and worms, but also detect attacks launched by external botnets in real time. The system can generate alarms and perform interception according to the configured strategies for these attacks.
In-depth defense against advanced threats
A variety of advanced threat attack and defense solutions are built-in, including AI-based advanced threat detection, behavior analysis-based abnormal threat detection, and linkage-based unknown threat detection, enabling multi-directional in-depth detection of and defense against advanced threats.
Comprehensive asset management
One-click asset scanning discovery, asset import and export, asset manual entry, asset linkage report, and asset categorization. It can identify assets and their different types based on the specified network scope through various ways such as automatic and manual identification. It provides asset risk assessment and asset behavior tracking on the basis of identifying assets, and ultimately helps administrators achieve asset protection and reinforcement.
Converged web application protection
The WAF security engine provides risk warning for malicious crawlers and intercepts their requests, effectively avoiding a surge in server CPU usage due to malicious crawlers, which may result in website service interruption. In addition, the WAF security engine is also provided with security capabilities such as the anti-leeching function, protection against CSRF, and application information hiding.
Converged HTTPS encrypted traffic detection
By providing SSL offloading, the system eradicates the blind spot where content security check (including virus filtering, URL filtering, content filtering, data filtering, and file filtering) and auditing cannot be performed on encrypted traffic, which can effectively prevent attackers from exploiting SSL encrypted traffic to launch malicious network attacks.
Threat maps and attack traceability
Not only can the threat map of each geographic location be displayed according to the IP address database, but also different access control strategies can be set according to different geographic locations. At the same time, the system supports attack traceability, with uninterrupted sensing of persistent threats, and can effectively block against the source of attacks, which can significantly reduce the impact of security incidents on user assets.
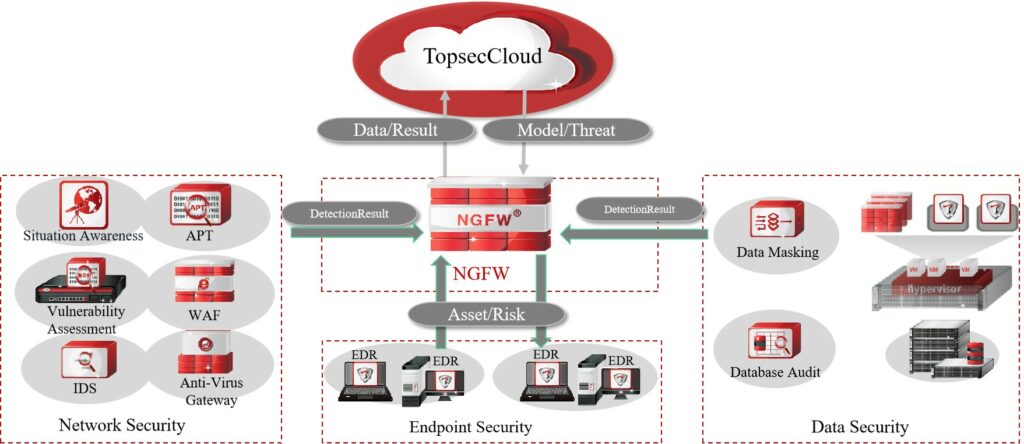
Application
Scenario
With NGFW as the core, through mobilization of the detection capabilities of other security components (such as IDS, APT, EDR, DLP, and situation awareness platform) on the network, real-time linkage, and collaborative sharing, an automated disposal system for global collaboration is formed. A proactive defense-in-depth system from single-point defense to global coverage is provided, which has linkage with terminals and the cloud, and implements global warning, coordinated protection, and risk visibility, helping customers implement pre-incident defense, control during incidents, and post-incident traceability for security threats.
- Enables granular, fine-grained application access control strategies for threat entrance reduction, illegal access prohibition, and resource abuse avoidance.
- Performs in-depth threat detection on traffic, blocking the implantation of viruses, Trojan horses, and bots to reduce security risks.
- Enables WAF application protection and function protection to safeguard web applications.
- Has collaboration and linkage with other security devices such as situation awareness and cloud detection to detect and block threats in real time, providing an in-depth defense solution.
- Enables the DLP function to prevent leakage of confidential documents and outgoing sensitive information.
- Makes good use of the asset management function for one-click asset discovery and protection.
Insight into network services
The system has rich visual display of traffic and threat trends to assist users in sensing network conditions.
Enhanced advanced protection
The system incorporates multiple security engines and advanced protection capabilities to provide comprehensive security protection.
Optimized intelligent management of O&M
The system provides rich platform-based and intelligent management tools to reduce user security operation costs.
Meeting diverse compliance requirements
The system complies with classified protection/hierarchical protection/industry standard specifications, and meets the requirements for operation and assessment compliance.